Creating a Maven Dependency Analyzer for Project Management
Introduction
As software developers, we often find ourselves juggling multiple projects. Each of these projects typically relies on numerous external dependencies that require regular updates to maintain security and take advantage of new features. After struggling to manage these dependencies manually across several projects, I decided to build a solution to automate and keep track of this process. This article describes how I created a Maven dependency analyzer to help track outdated dependencies, vulnerabilities, and license issues.
Maven: A Quick Introduction
Maven, originating from a Yiddish word meaning "accumulator of knowledge," was initially created to simplify the build processes in the Jakarta Turbine project. At the time, different projects had their own Ant build files with minor differences, and JAR files were manually stored in CVS. The aim was to establish a unified build system, provide a clear project structure, streamline the publication of project details, and facilitate JAR sharing across multiple projects.
The result was a powerful tool designed to build and manage any Java-based project efficiently. It was developed to improve developers' daily workflows and enhance the overall comprehension of Java projects.
Maven is a build automation tool used primarily for Java projects. One of its key features is dependency management. Maven downloads and links the libraries of your project based on declarations in a Project Object Model (POM) file.
Why I Built a Custom Analyzer
When you create and maintain many projects simultaneously, it's challenging to keep track of every dependency manually. After trying to maintain dependencies by hand, I realized I needed an application to inspect and review updates and vulnerabilities of my dependencies.
Specifically, I wanted to:
- Automate checking for newer versions of dependencies
- Identify potential security vulnerabilities
- Track dependency status over time
- Visualize the health of my projects' dependencies
- Get notifications when critical updates were available
I wanted something tailored exactly to my workflow that could integrate with my existing projects.
Designing the Application
I established several key requirements for my dependency analyzer:
- Project-based organization — Group analyses by project for better organization
- Historical tracking — See how dependencies change over time
- Visualization — Generate charts to visualize dependency status
- REST API — Enable integration with CI/CD pipelines
- Vulnerability detection — Flag dependencies with known security issues
- Local file access — Analyze POM files directly from my filesystem
- Containerized deployment — Run the application in Docker for easy setup
Technical Architecture
I decided to build a Spring Boot application. For the tech stack, I chose:
- Java 21 for the backend
- Spring Boot 3 for the application framework
- MySQL for persistent storage
- Redis for caching
- JFreeChart for visualization
- Docker for containerization
Key Features Implemented
POM Parsing and Analysis
The core functionality revolves around parsing POM files and extracting dependency information. I implemented two approaches:
- Direct file access — Parse POM files from local filesystem
- Content submission — Allow uploading POM content via API
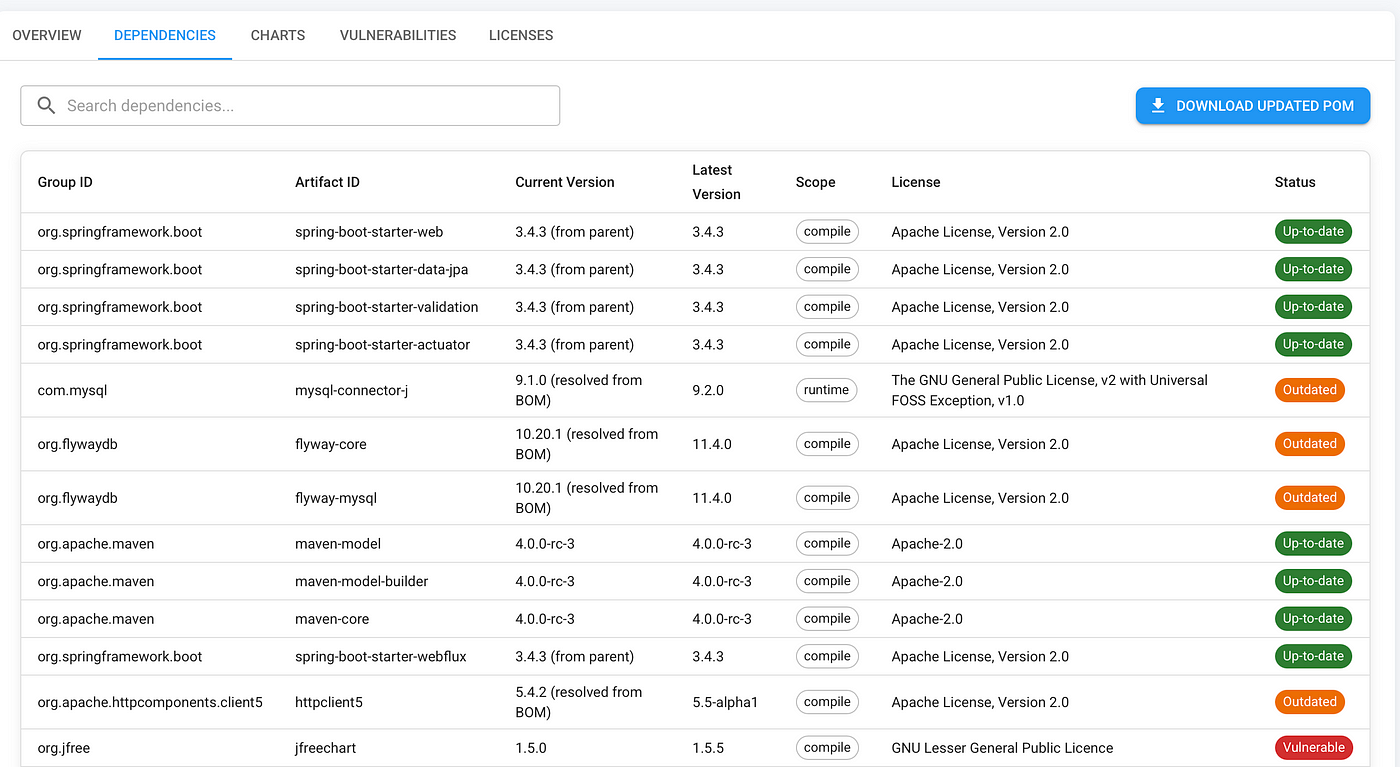
The parser extracts group IDs, artifact IDs, and versions, then checks against Maven Central to determine if newer versions are available.
public List<DependencyInfo> analyzeDependencies(String pomContent) {
Document pomDocument = parsePomContent(pomContent);
List<DependencyInfo> dependencies = extractDependencies(pomDocument);
for (DependencyInfo dependency : dependencies) {
checkForNewerVersions(dependency);
}
return dependencies;
}
Version Comparison Logic
One of the more interesting challenges was implementing version comparison logic. Maven version strings follow complex rules, and comparing them correctly required careful implementation:
public boolean isNewer(String currentVersion, String latestVersion) {
// Handle special cases like SNAPSHOT versions
if (currentVersion.endsWith("-SNAPSHOT")) {
currentVersion = currentVersion.replace("-SNAPSHOT", "");
}
// Convert to ComparableVersion for proper comparison
ComparableVersion current = new ComparableVersion(currentVersion);
ComparableVersion latest = new ComparableVersion(latestVersion);
return latest.compareTo(current) > 0;
}
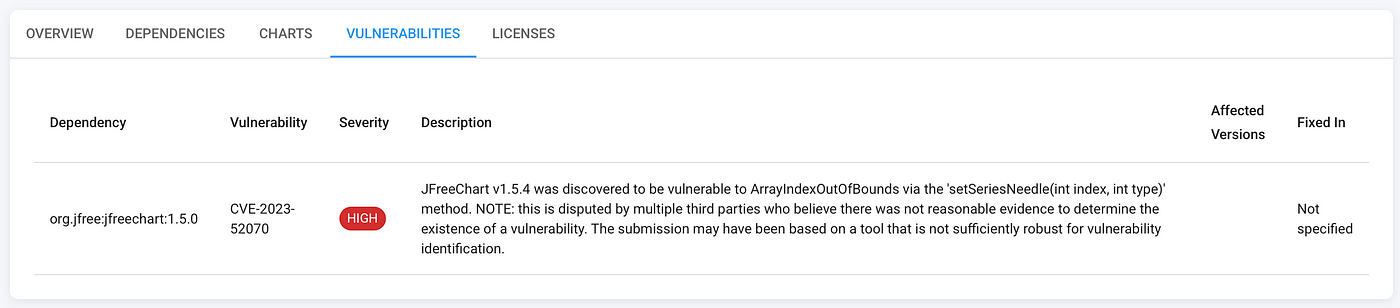
Vulnerability Detection
For vulnerability detection, I integrated with the OSS Index API to check if any dependencies had known security issues:
public Map<String, List<VulnerabilityInfo>> checkVulnerabilities(List<DependencyInfo> dependencies) {
List<String> coordinates = dependencies.stream()
.map(this::formatDependencyKey)
.collect(Collectors.toList());
// Call OSS Index API to check for vulnerabilities
ResponseEntity<List<OssIndexResponse>> response =
ossIndexClient.checkVulnerabilities(coordinates);
return processOssIndexResponses(response.getBody());
}
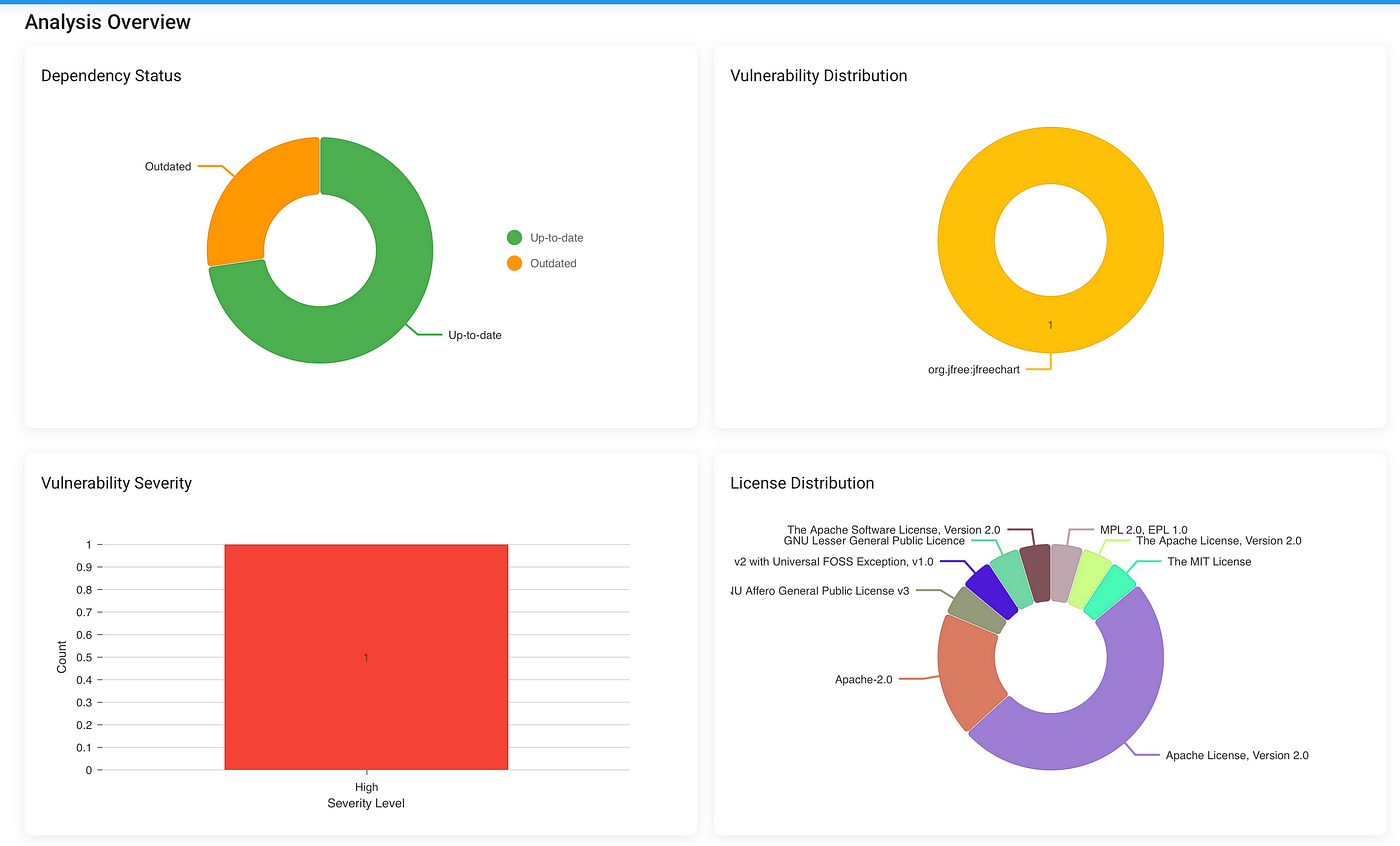
Visualization with Charts
To make the data more digestible, I implemented chart generation using JFreeChart:
public String generateDependencyStatusChart(AnalysisResult analysis) {
DefaultPieDataset<String> dataset = new DefaultPieDataset<>();
dataset.setValue("Up to date", analysis.getUpToDateDependencies());
dataset.setValue("Outdated", analysis.getOutdatedDependencies());
dataset.setValue("Unidentified", analysis.getUnidentifiedDependencies());
JFreeChart chart = ChartFactory.createPieChart(
"Dependency Status", dataset, true, true, false);
return saveChartToFile(chart, analysis.getId());
}
Implementation Challenges
Access to Local Filesystem from Docker
One significant challenge was accessing local POM files when running the application in Docker containers. The containerized backend couldn't access files on the host filesystem without special configuration.
I solved this by implementing a hybrid deployment approach:
- Run the UI, MySQL, and Redis in Docker containers
- Run the backend directly on the host for file access capabilities
This compromise worked well for my development workflow while still leveraging containerization for most components. I plan to implement other solutions about this section in future parts.
Caching Optimizations
Another challenge was performance. To avoid making repeated calls to Maven repositories for license information, I implemented caching:
@Cacheable(value = "licenseCache", key = "#groupId + ':' + #artifactId + ':' + #version",
unless = "#result.isEmpty()", condition = "#root.target.licenseCacheEnabled")
public Optional<String> fetchLicenseInfo(String groupId, String artifactId, String version) {
// Fetch license info from Maven repository
}
This significantly improved analysis speed for repeated checks of the same dependencies.
What's Next
In the next parts of this series, I'll cover:
- Implementing notification systems for critical updates
- Containerization improvements
- Extending support for multi-module Maven projects
- More detailed caching explanation
- Implemented logic to reduce API calls
- Settings and customization
- Improved version comparison
The full source code for this project is available on my GitHub. Code examples in the snippets are simplified for educational purposes.
Thank you for reading, and happy coding!
